In part two of the Cosmic-X blogpost series, we explained how we use the Secret Network blockchain and a custom Wallet Service to ensure the integrity and privacy of machine-generated data in Industry 4.0 environments. In this final part, we’ll show how we integrated the Wallet Service with live machines from SW and an AI service from inovex. Together, they power a proof-of-concept demonstrator for secure and accurate anomaly detection in machine components.
Visualizing Sensor Data
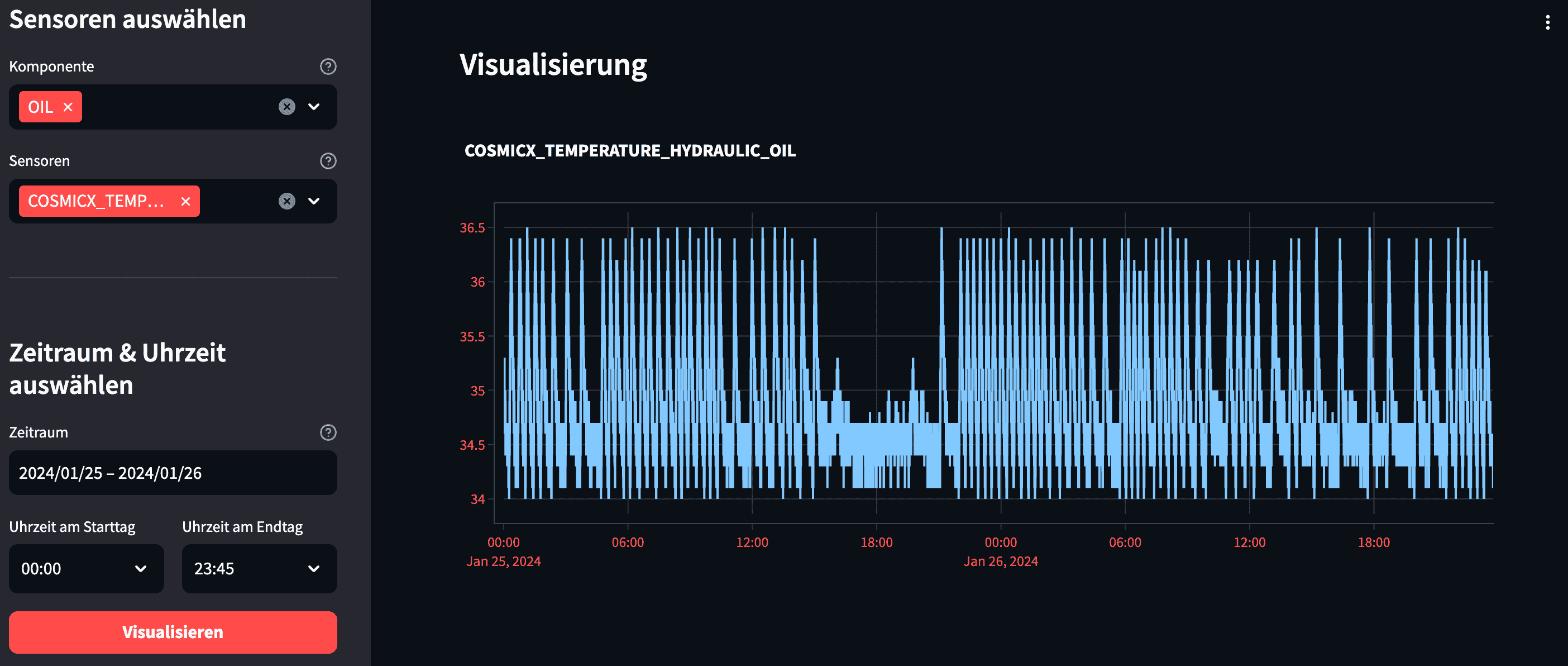
The demonstrator has three core features. First, the data exploration tool lets you visualize sensor data from three different machines. For granularity, you can filter by machine, component, sensor, and the timeframe you want to monitor.
Verification & Anomaly Detection
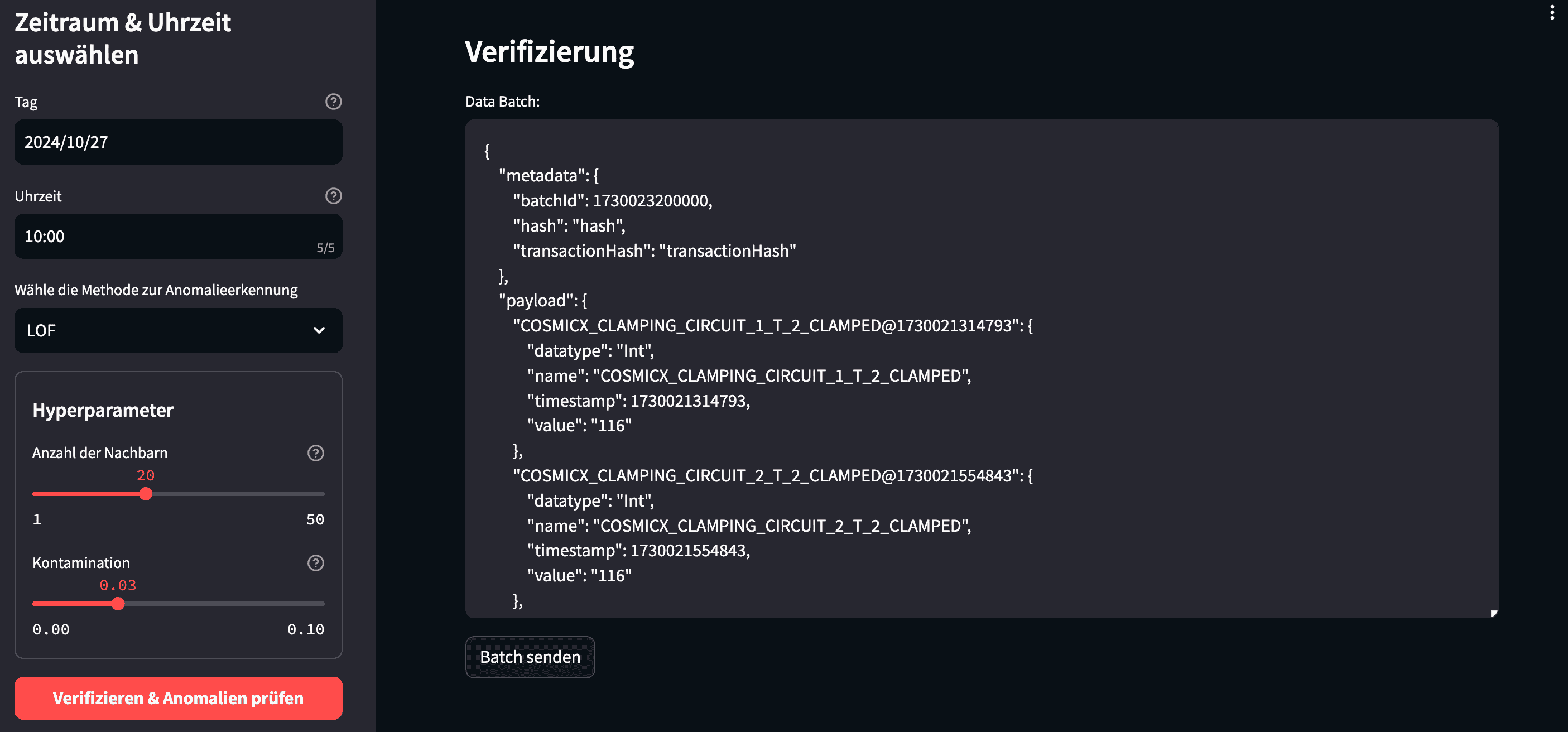
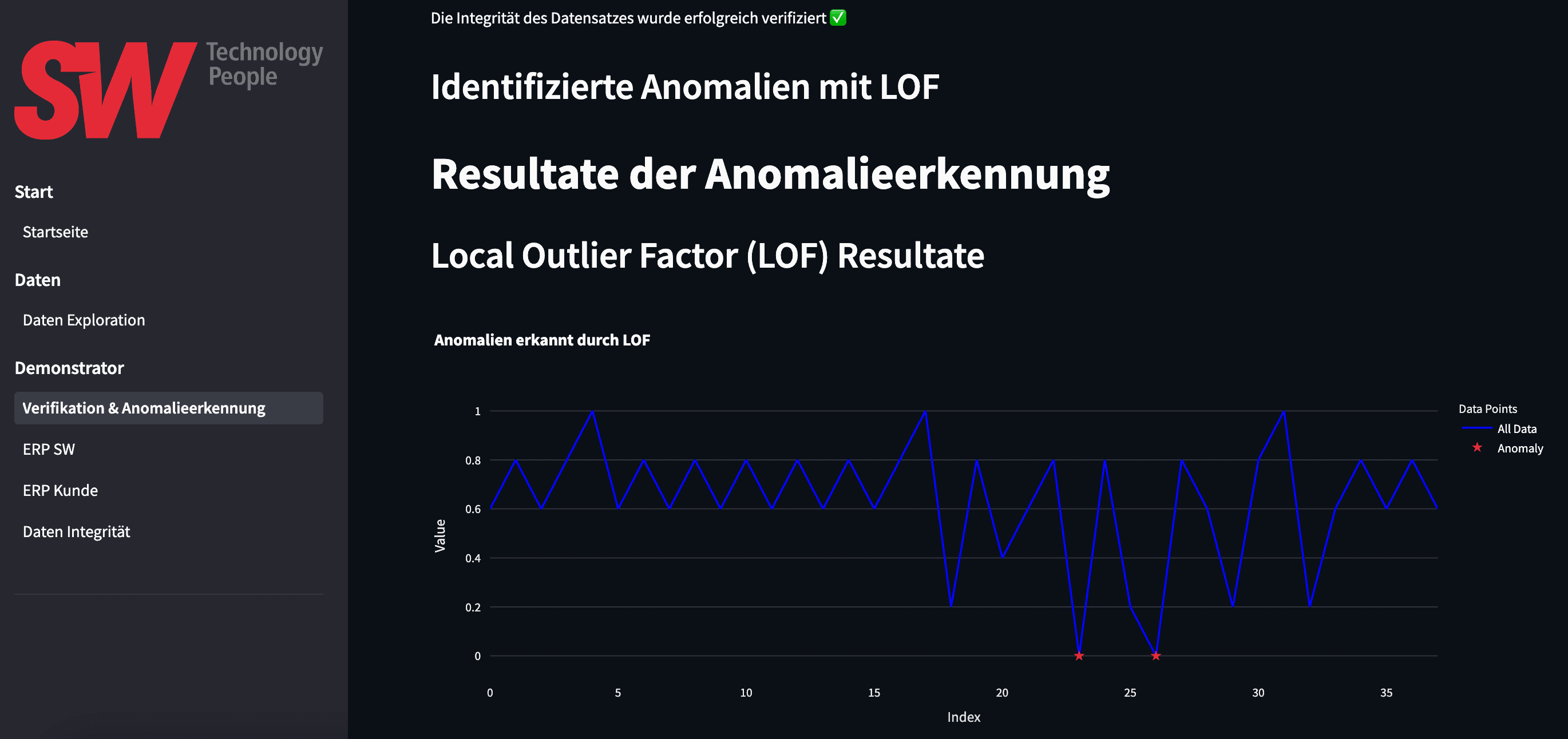
Next, the anomaly detection feature, coupled with data integrity verification. Like before, you can filter by machine, component, sensor, and timeframe. Additionally, you choose from three anomaly detection algorithms—Local Outlier Factor (LOF), DBSCAN, and Isolation Forest—and adjust their hyperparameters. After that, once you lock in your configuration and submit the query, the system fetches data from a central time series database. It then converts the data into the standardized format described in our previous post.
To ensure trust, the Wallet Service verifies the dataset by comparing a freshly generated fingerprint to the one anchored on the blockchain. It uses the standardized batchID for this lookup. If the fingerprints match, the AI service proceeds with the anomaly detection. Whenever the number of anomalies exceeds a defined threshold, the system flags the component as worn out. Consequently, it submits an automatic spare part order to the ERP systems of the manufacturer and the customer.
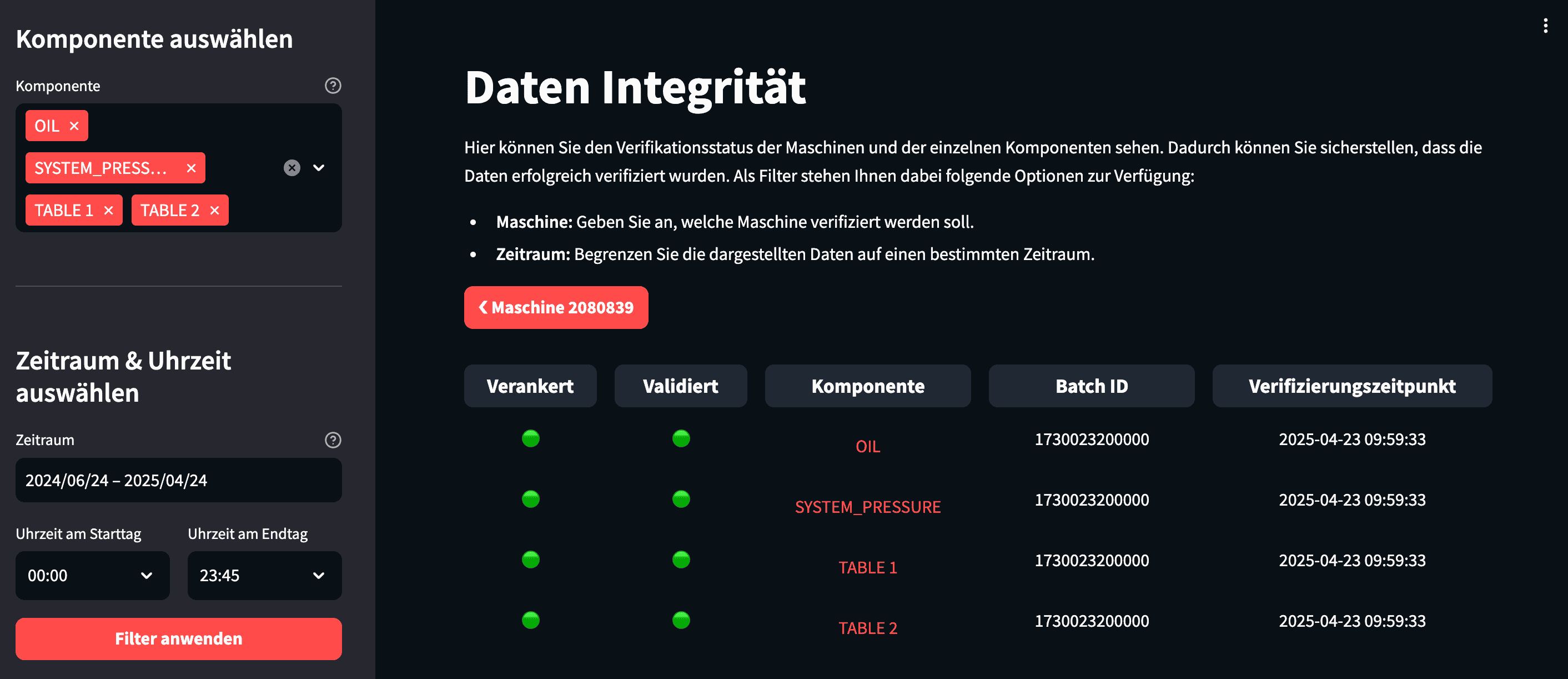
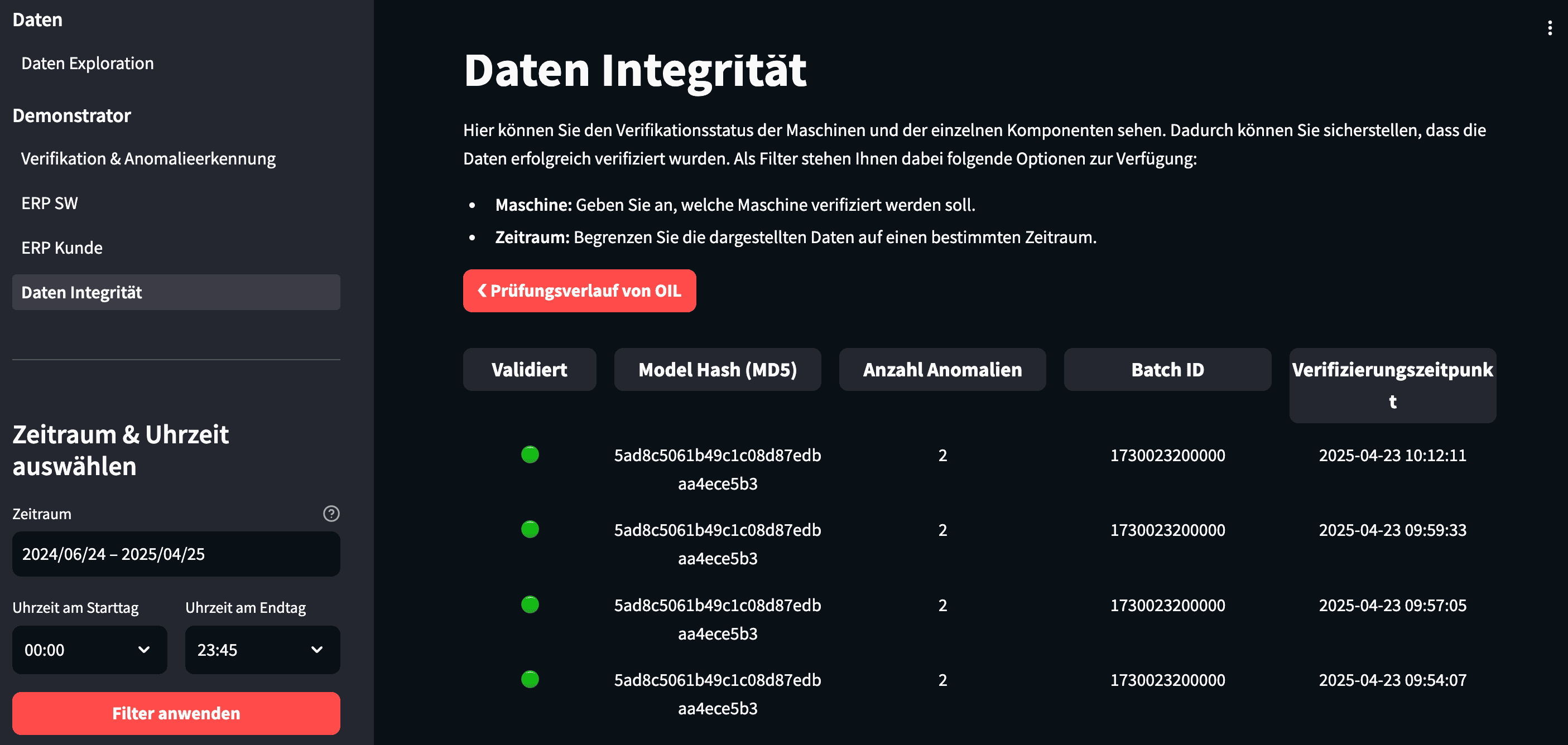
Data Integrity Log
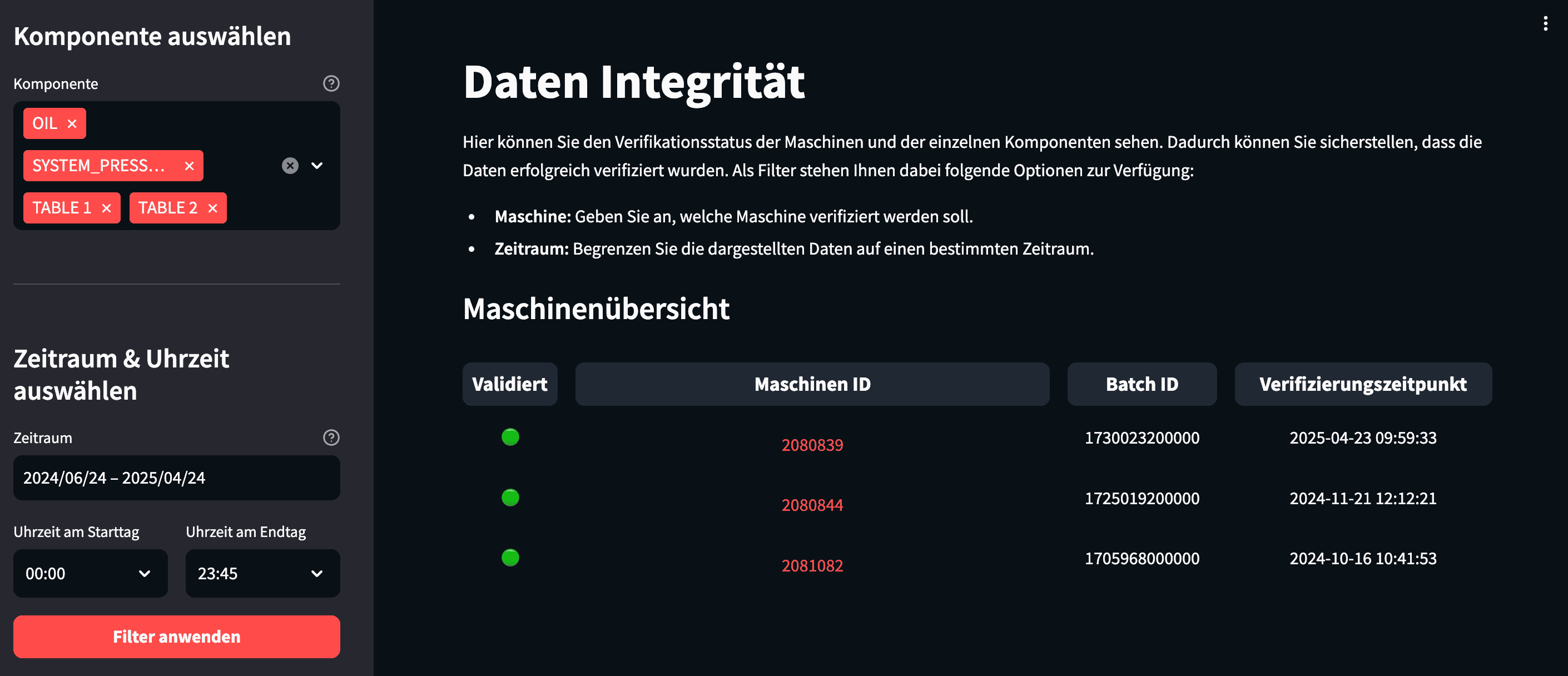
In this demonstrator, users manually trigger the configuration and execution of the anomaly detection. In contrast, a production system would automate and continuously run these steps. The third feature is a data integrity log to give users better visibility of what is happening. This audit trail has three levels: At the top level, it shows the health status of each machine and the last verified batch used for anomaly detection.
Next, it breaks down each machine into components, displaying health statistics for each
Finally, it presents detailed logs of every anomaly detection run and whether the data integrity check succeeded.
As we wrap up this blog post series, what began as a technical experiment has evolved into something much broader. It points toward a future of industrial intelligence that values transparency and built-in trust. By embedding trust directly into machine data and equipping AI with verified information, we do more than detect anomalies. We enable machines to communicate, collaborate, and maintain themselves. Ultimately, this proof of concept is a first step toward an Industry 4.0 landscape that is autonomous, secure, and transparent, where trust is not an afterthought but a foundation.
Curious how our blockchain-based data-integrity solution can help your business? Check out our one-pager for a quick overview of its key benefits!