With the Cosmic-X project nearing its conclusion, it is finally time to lift the curtain on the blockchain solution that Datarella has built over the last two years to enable confidential computing and data sharing in Industry 4.0. In this first entry of a series of technical posts about designing, implementing, and integrating an edge-to-cloud blockchain solution, we discuss the evaluation process for selecting a suitable blockchain platform for Cosmic-X and how that platform operates on a protocol level to provide an open, transparent, and secure infrastructure for industrial use cases.
Evaluating Blockchain Platforms
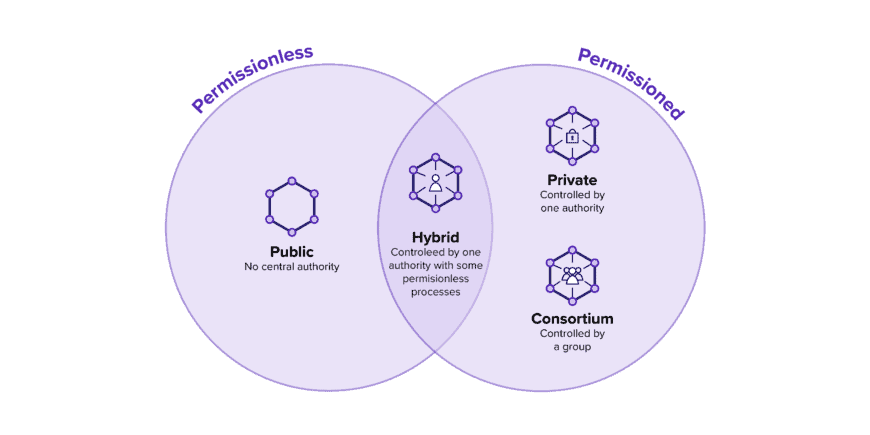
Today, many different blockchain platforms exist, but their suitability for industrial use cases remains specific or, at times, limited. To achieve the best match between the requirements of Cosmic-X and the possibilities of blockchain technologies, the team conducted an extensive evaluation process. This evaluation compared both private and public blockchain platforms based on security, privacy, scalability, and interoperability.
Current-generation blockchain platforms predominantly perform well in security and scalability, yet privacy and interoperability often fall short. To achieve privacy in industrial scenarios like Cosmic-X, organizations have almost exclusively used private or consortium blockchains such as Hyperledger Fabric in the past. However, these approaches inherently involve high infrastructure costs for the operating parties, as well as centralization and limited interoperability. In contrast, public blockchains offer resilience, cost efficiency, and a degree of interoperability. Though only recently have they started focusing on privacy and data protection. Blockchain protocols with confidential computing capabilities remain relatively new and untested. Nevertheless, when weighing the advantages and disadvantages of the two approaches, a privacy-focused public network emerges as the preferred solution in an industrial context.
For a public network to meet Cosmic-X’s privacy and data protection requirements, it must support the multi-tenancy paradigm. Multi-tenancy enables a single instance of a software application to serve multiple clients while ensuring logical isolation. Different clients share an underlying infrastructure, which optimizes resource use and reduces infrastructure costs. Further, it enhances efficiency in data access, management, and collaborative data sharing.
Through this evaluation, the Cosmos-based Secret Network emerged as the blockchain platform best suited for Cosmic-X. The Secret Network functions as a public blockchain specifically developed for confidential computing. By combining established encryption techniques with trusted execution environments, it provides so-called Secret Contracts. This type of smart contract establishes consensus on computation without disclosing incoming or outgoing data. Integrated access control mechanisms enable third-party access and create an auditable processing chain. Thus, the Secret Network satisfies the need for multi-tenancy capability while retaining all the benefits of a public network.
How the Secret Network Works
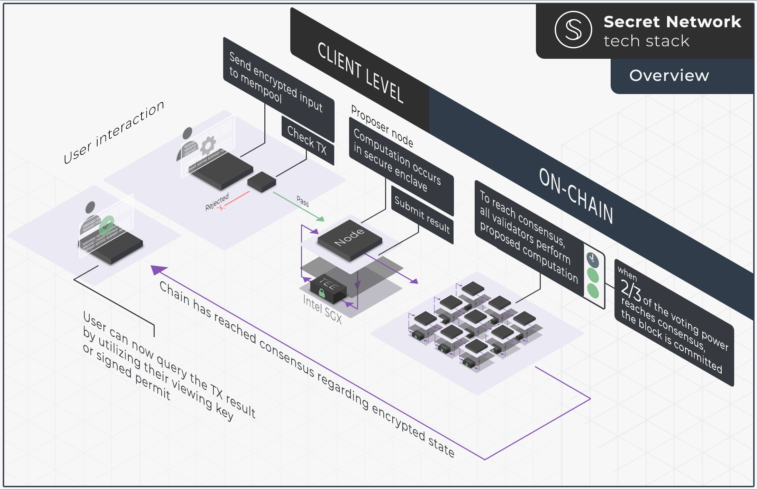
The Secret Network leverages Intel Software Guard Extensions (Intel SGX) to create Trusted Execution Environments (TEE) that enable Secret Contracts. These smart contracts, based on the CosmWasm framework, allow for fully private computation of data. Outside a TEE, the transaction payloads and the network’s current state are encrypted at all times. Only the data owner and an authorized third party can decrypt and view data inputs and outputs. A combination of symmetric and asymmetric encryption schemes—ECDH (x25519), HKDF-SHA256, and AES-128-SIV—achieves this end-to-end encryption. Each validator in the network must run an Intel SGX-compatible CPU and instantiate a TEE that follows the network’s rules.
When an encrypted transaction arrives in the shared mempool of the network, a validator forwards it to their TEE, where a shared secret is derived and used to decrypt the transaction. The WASMI runtime then processes the plaintext input. Finally, the validator re-encrypts the updated contract state and broadcasts it to the network through a block proposal. If over two-thirds of the current network voting power agree on the result, the network appends the proposed block to the Secret Network blockchain.
For access control, the Secret Network offers Viewing Keys and Permits. A Viewing Key acts as an encrypted password that grants a third party permanent access to data related to a specific smart contract and private key. A Permit allows a more granular approach, restricting viewing access to specific parts of data for a set period. Consequently, despite its encrypted nature, the network remains fully auditable.
In the next post, we’ll explore how we leverage the Secret Network to secure machine data integrity directly from its point of origin to its consumption by a Machine Learning Model.